SOC Automation - Wazuh Agent Configuration and Sysmon Integration
In this blog post, I’ll walk through how I configured a Wazuh agent in my SOC automation project. This included enabling the ingestion of Sysmon events and creating custom alerts in Wazuh to detect specific malicious activities, such as the execution of Mimikatz using its original file name.
Setting Up the Environment
To start, I configured the Windows 11 machine to generate telemetry that could be ingested into Wazuh for analysis. The telemetry logs were generated by Windows, Sysmon, and other services, and I directed these logs to Wazuh for monitoring.
Editing the Configuration File
I opened the ossec.conf file with administrative privileges using Notepad (C:\Program Files (x86)\ossec-agent\ossec.conf)
Sysmon (System Monitor) is a powerful tool that I used to monitor and log detailed information about system processes and network connections. This tool was essential for detecting malicious activities such as Mimikatz execution.
I launched Event Viewer by typing “Event Viewer” in the Start menu. I navigated to the following location to find the Sysmon logs:
1
Applications and Services Logs → Microsoft → Windows → Sysmon → Operational
Right-clicking on Operational, I selected Properties and copied the full channel name (e.g., Microsoft-Windows-Sysmon/Operational).
In the ossec.conf file, I located the log analysis section and added Sysmon logs for ingestion:
1
2
3
4
<localfile>
<location>Microsoft-Windows-Sysmon/Operational</location>
<log_format>eventchannel</log_format>
</localfile>
After performing the changes, I navigated into Services and restarted the Wazuh Service. This ensured that the changes were applied and Sysmon event logs were ingested by Wazuh.
Create a Custom Rule to trigger an Alert
Sysmon captures Event ID 4688, which I used to monitor process creation.
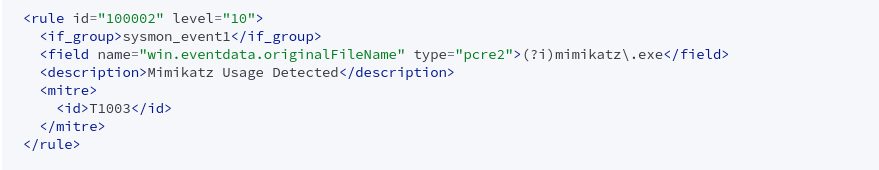
I navigated to the Wazuh CLI and located the rules folder. Then I added a custom rule for Mimikatz detection by copying an existing Sysmon rule and modifying it making sure that the eventid is over 100001 and adding the needed pcre2 regex:
I have also added the mitre Id for credential dumping (T1003) This rule monitored for the original file name “mimikatz.exe” and triggered an alert if Mimikatz was detected.
After adding the custom rule, I restarted the Wazuh Manager for the changes to take effect.
Ingesting Logs and Configuration
To ingest logs into Wazuh for analysis, I configured Filebeat to collect and forward the log data.
In the /var/ossec/etc/ossec.conf file under the wazuh server, I ensured that the following parameters were enabled to archive all logs:
1
2
<log_all>yes</log_all>
<log_json>yes</log_json>
I updated Filebeat to forward these logs by editing its configuration file:
1
nano /etc/filebeat/filebeat.yml
I located the section dealing with archives under filebeat.modules and set archives → enabled to true. To apply the changes I proceeded to restart the Filebeat service:
1
systemctl restart filebeat
Mimikatz Detection and Security Event Monitoring
Mimikatz is a well-known tool used by attackers to extract credentials from Windows machines. In this setup, I configured Wazuh to monitor Sysmon logs for Mimikatz execution.
Before testing Mimikatz, I excluded the Downloads folder from Windows Defender to prevent the tool from being blocked:
1
Windows Security → Virus & Threat Protection → Manage Settings → Exclusions → Add Folder → Select Downloads
I then downloaded Mimikatz from gentilkiwi/mimikatz, extracted the files, and ran the executable from an elevated PowerShell session:
1
2
cd C:\Users\YourUser\Downloads\mimikatz_trunk\x64
.\mimikatz.exe
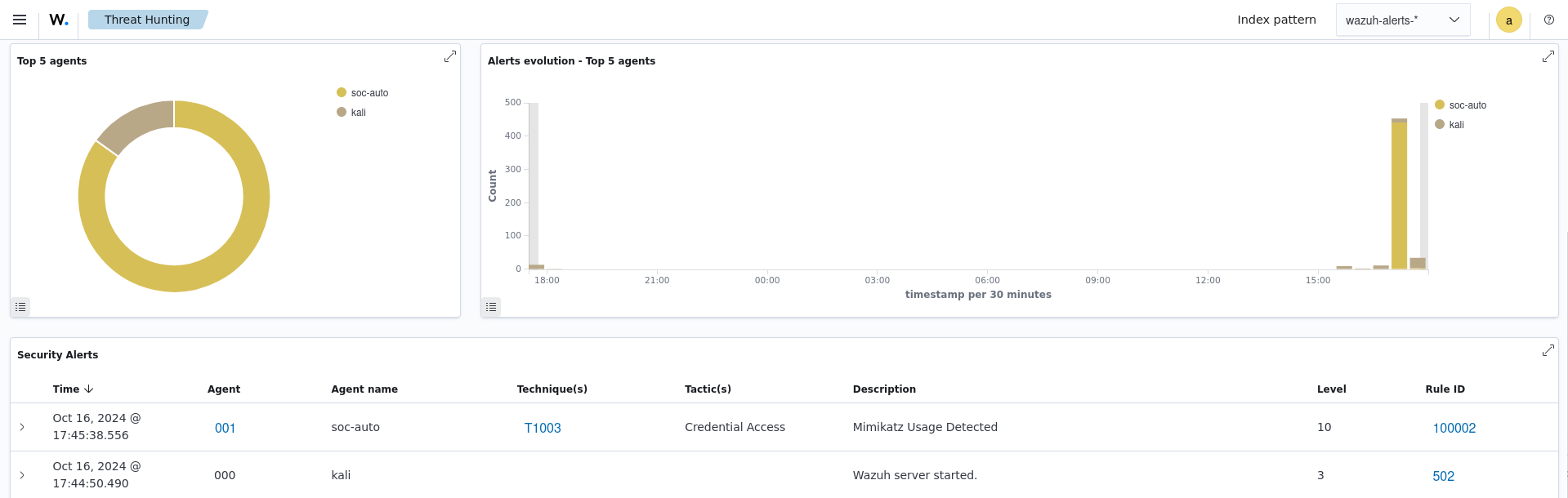
In the Wazuh Dashboard we could see that the Mimikatz Alert we created was triggered with the mitre ID and description I had configured:
Conclusion
By configuring Wazuh, Sysmon, and setting up Mimikatz detection, I enhanced the security monitoring in my SOC automation project and gained hands on experience in doing. This setup allowed for the automation of detecting Mimikatz based threats by monitoring logs, setting up custom alerts, and utilizing Sysmon’s detailed event logs.
These configurations are essential for cybersecurity professionals aiming to automate SOC operations and stay ahead of potential attackers.
Next Steps
Now that we are able to trigger an alert in Wazuh, next we need to forward that alert to The Hive and an email alert, after passing the event through Shuffle (the SOAR tool).
This post is part of Jad’s Cybersecurity Blog.